Alberto Marmolejo-Daher, Cody Eckhoff, Justin Moore – March 29, 2024
Privacy Policies are an organization’s outline of how consumer data is aggregated, analyzed, stored, and protected. In this reading, we’re going to outline what these policies are and connect them to cybersecurity.
Historically the United States has allowed businesses and institutions to collect the personal information of its users without express consent, while regulating those in specific sectors like medical and educational via the following acts: Health Insurance Portability and Accountability Act (HIPAA), Family Educational Rights and Privacy Act (FERPA), and Children’s Online Privacy Protection Act (COPPA).
It’s important to recognize that regulations are under constant development because of how rapidly technology has been developed. The European Union adopted regulations in 2018 called the General Data Protection Regulation or GDPR that impose obligations on organizations anywhere. Here is a good article that explains how EU GDPR applies in the USA. Since 2023, states in the USA are beginning to enforce GDPR-like statues, states including California, Colorado, Utah, and Connecticut. These laws will change how US companies handle your data, please read the hyperlinked article for more detail.[Mo1]
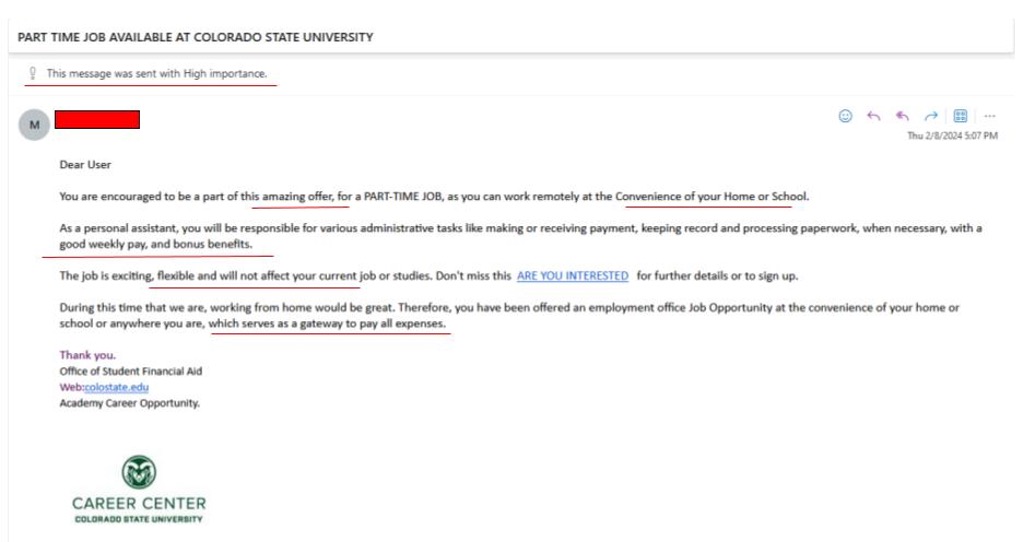
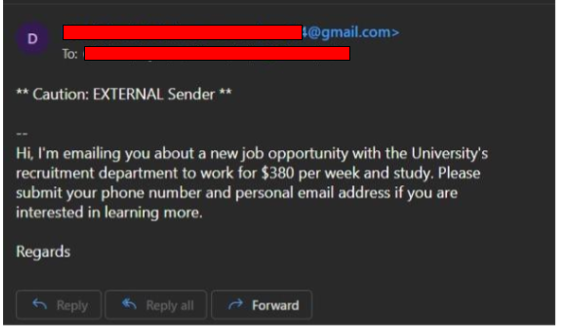
Organizations such as TikTok, Meta, and X (formerly known as Twitter) all have privacy policies that are meant to be transparent to consumers on how their data is managed. While different, they are foundationally the same. These policies generally include what information is collected, what information is shared with third parties, how that information is shared, and how long they keep your information. For example, Meta collects your feed activity, messages sent and received, payment information, preferences, geolocation, and more.[Mo2] You can easily find these policies by searching “<company name> privacy policies” in a search engine.
Now that we’ve reviewed how privacy laws are ongoing and relevant, we can better understand how they relate to your information online. There have been many data compromises in recent years and a lack of transparency from organizations when data breaches occur. The Digital Guardian has a good article on the laws about disclosure of breaches, if you’re willing to read about them (I know it’s boring, but a quick skim of the text won’t hurt). Apple has a feature on their devices (if you store your passwords in their keychain) that notifies you if your account has appeared in a data breach. Also, you can use a website called haveibeenpwned to check if your email has been included in a data breach.
In cybersecurity, we have some key terms to identify data types that appear frequently in privacy policies. Some of these you may have heard of:
- PII: Personally Identifiable Information
- SPII: Sensitive Personally Identifiable Information
- PHI: Protected Health Information
In addition to these terms, here are five recommendations for protecting your privacy and data.
- Don’t post PII on your social media, as it may be used to reset your password through security questions such as the names of pets, relatives, high school mascots, etc.
- Generally, organizations collect sensitive data; it’s important to be cautious when choosing usernames and passwords because if their data is breached, your data will be breached.
- When choosing usernames, do not choose anything that can be linked to you in a way that could be used for more personal data.
- Do not reuse passwords for multiple accounts. What if a threat actor gains access to your Facebook account using the same user and password as your bank account?
- Enable Multifactor Authentication (MFA), also known as 2-factor authentication on your devices and accounts. This mitigates an incident where your password is compromised by requiring a second layer of security, such as biometrics, push notifications, etc.[Mo3]
Intro [Mo1]
Social Media/ General Company Handling [Mo2]
MFA, SPII, PII, PHI [Mo3]